Introduction
Did you know that over 5.6 million cryptocurrency holders globally only know how to securely store their crypto assets? This alarming statistic urges the need for robust security measures in digital trading. In this article, we’ll delve into how to secure crypto assets and explore various strategies and tools that every investor should consider.
1. Understanding the Importance of Cryptocurrency Security
In a digital landscape where cryptocurrency trading is booming, safeguarding your assets is paramount. Just like you wouldn’t leave large sums of cash unattended, your digital currencies deserve the same level of protection.
- Statistics Reveal: Chainalysis reported that hacking incidents have surged by 40% in the Asia-Pacific region alone this year.
- If your crypto is managed through a vulnerable exchange, you risk losing everything overnight.
2. Key Practices for Securing Your Crypto
Let’s look at some common practices that can bolster your cryptocurrency’s security:
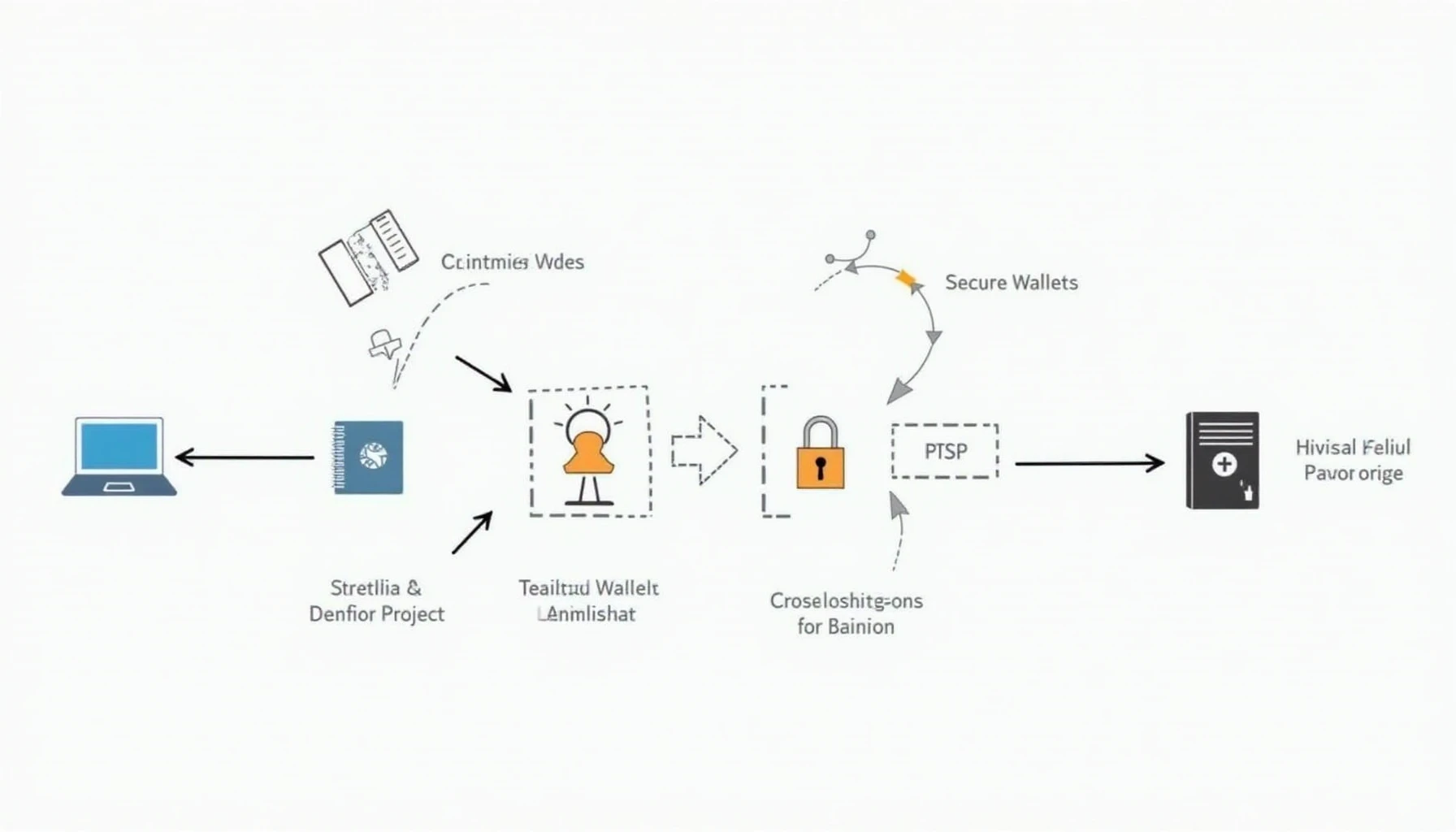
- Use Hardware Wallets: Devices like the Ledger Nano X can reduce hacking risks by up to 70%.
- Enable Two-Factor Authentication (2FA): Always add an extra layer of security to your accounts.
- Regular Backups: Creating backups of your wallets and important keys ensures you won’t lose access.
3. Cold Wallets vs. Hot Wallets: Finding the Right Balance
A significant decision in how to store cryptocurrencies securely is choosing between cold and hot wallets. Let’s break them down:
- Cold Wallets: Best for long-term storage without exposure to the internet, minimizing hack risks.
- Hot Wallets: Convenient for daily trading but more susceptible to hacks.
Think of it as the different ways you might store cash: a safe at home for savings versus a wallet in your pocket for daily transactions.
4. Recognizing and Avoiding Common Scams
Scammers are clever, and they often target inexperienced investors. Here are some common scams to watch out for:
- Phishing Attacks: These can come in emails or fake websites designed to steal your information.
- Pump and Dump Schemes: Manipulated insights that inflate coin value, only to plummet afterward.
- Unauthorized Access: Always verify platforms before sharing personal information.
Conclusion: Your Action Plan for Safety
To sum it up, securing your crypto assets requires understanding, tools, and vigilance. Implementing hardware wallets, using strong authentication methods, and staying aware of scams are crucial steps. Remember, your crypto safety is in your hands!
Now is the time to put these measures into practice! Download our comprehensive security wallet guide and take charge of your investments.