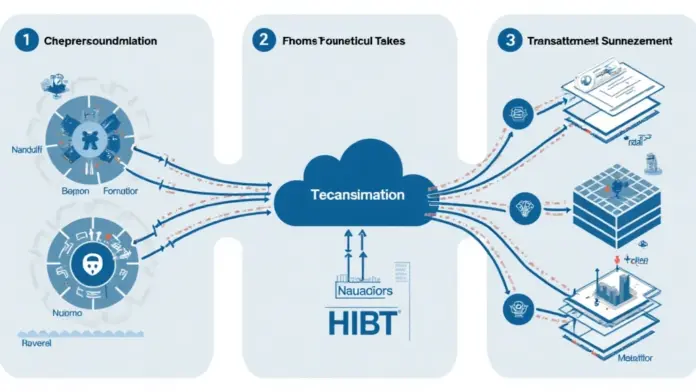
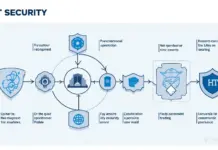
What Are HIBT Security Model Diagrams?
Have you ever wondered how cryptocurrency transactions ensure safety against cyber attacks? According to a recent survey, over 60% of cryptocurrency users lack knowledge about secure transaction practices. This is where HIBT security model diagrams come into play, providing a clear representation of security protocols in digital currencies.
Key Components of HIBT Security Models
Understanding HIBT models is crucial to grasp the essence of secure cryptocurrency transactions. Think of it like a recipe for baking a cake: without the right ingredients and instructions, the cake might fail. Similarly, HIBT models outline essential components that contribute to robust security:
- Authentication: Ensuring that users are who they claim to be.
- Encryption: Protecting sensitive data through complex algorithms.
- Access Control: Limiting who can access which parts of the system.
- Monitoring: Continuous surveillance for any irregular activities.
How HIBT Models Help Secure Cryptocurrency Transactions
Many newcomers to cryptocurrency may feel overwhelmed by the security aspects. Here’s a simple analogy: consider your funds like a precious jewel. You wouldn’t leave it on your kitchen counter, right? Instead, you’d invest in a safe. HIBT security models function like that safe, offering layers of protection:
- Preventing Fraud: They minimize the risk of unauthorized transactions.
- Enhancing Trust: These models promote user confidence in the blockchain ecosystem.
- Compliance with Regulations: They help users align with local laws, like the Singapore cryptocurrency tax guide.
Practical Tips for Implementing HIBT Security Measures
Now that you understand the importance of HIBT models, let’s explore some practical steps to integrate these measures into your cryptocurrency transactions:
- Use Strong Passwords: Opt for unique, complex passwords to protect your accounts.
- Enable Two-Factor Authentication: Adding another layer of security significantly reduces risks.
- Regularly Update Security Software: Outdated systems are more vulnerable to attacks.
- Educate Yourself: Stay informed about the latest developments in cryptocurrency security.
Conclusion: Secure Your Digital Assets Today
In conclusion, understanding the HIBT security model diagrams is essential for anyone engaging in cryptocurrency transactions. By implementing the recommended security measures, you can significantly lower your risks of fraud and cyber attacks. So, what are you waiting for? Start educating yourself today and make your cryptocurrency journey a secure one!
For further resources, check out our comprehensive guides on security best practices.