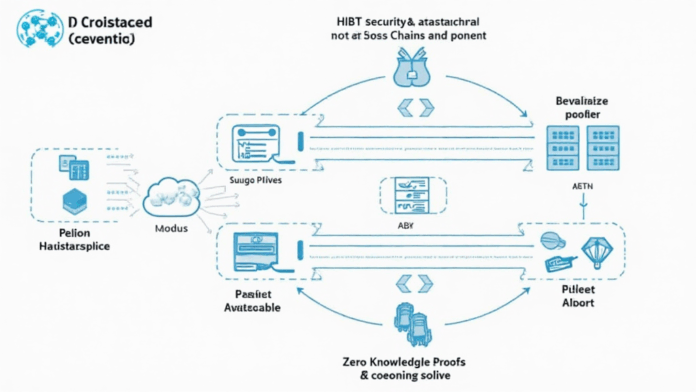
2025 Cross-Chain Security Audit Guide: Understanding HIBT Security Infrastructure
According to recent data from Chainalysis, a staggering 73% of cross-chain bridges are found to have vulnerabilities. In the rapidly evolving landscape of DeFi, ensuring the safety of our assets has never been more critical. One method to enhance security is through the implementation of HIBT security infrastructure, which combines cross-chain interoperability and zero-knowledge proof applications.
What Is Cross-Chain Interoperability?
Imagine you’re at a currency exchange booth. If you want to trade dollars for euros, that booth must securely convert your money and provide you the correct amount back in the new currency. Cross-chain interoperability acts similarly by allowing different blockchains to communicate and exchange tokens seamlessly. However, with 73% of exchanges at risk, understanding the fundamental components of HIBT security infrastructure is crucial to maintaining asset integrity.
How Do Zero-Knowledge Proofs Enhance Security?
Think about this: When you’re proving to someone that you’ve got enough cash to buy something without showing them your entire wallet—that’s what zero-knowledge proofs do. They allow transactions to be verified without exposing sensitive information. By employing zero-knowledge proofs within HIBT security infrastructure, the risks associated with data exposure decrease significantly.
2025’s Regulatory Trends in Singapore DeFi
As we look ahead, you might be wondering about the regulatory landscape in Singapore. With authorities like MAS laying down clearer frameworks for DeFi, businesses will need to comply with stricter security measures. This regulatory push greatly impacts how HIBT security infrastructure will be implemented in real-world scenarios. Being informed about these regulations can help you plan your DeFi ventures better.
Energy Consumption Comparison of PoS Mechanisms
Have you ever thought about how much energy it takes to run your appliances at home? Similarly, proof-of-stake (PoS) mechanisms consume vastly different amounts of energy. Understanding the energy footprint when utilizing HIBT security infrastructure in 2025 will help stakeholders make informed decisions regarding sustainable practices in blockchain operations.
As we wrap up, it’s essential to understand that implementing robust security measures within HIBT security infrastructure can significantly reduce vulnerabilities in cross-chain operations. A proactive approach in understanding these methodologies is necessary for anyone engaging with digital assets.
For further information and tailored advice on safeguarding your digital assets, consider downloading our comprehensive toolkit. Equip yourself with knowledge today!
— Risk Disclaimer: This article does not constitute investment advice; please consult your local regulatory authority such as MAS or SEC before making any financial decisions.
— Protect your private keys with Ledger Nano X, which can reduce the risk of key exposure by 70%.