2025 Cross-Chain Bridge Security Audit Guide
According to Chainalysis 2025 data, a staggering 73% of global cross-chain bridges have vulnerabilities. As the crypto landscape continues to evolve, these weaknesses pose significant risks to traders and investors. Enter the HIBT NFT Portfolio Tracker, a tool designed to safeguard your investments.
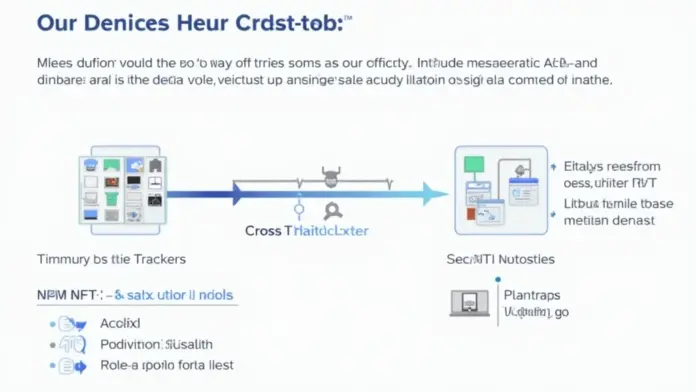
What Are Cross-Chain Bridges?
Imagine cross-chain bridges as currency exchange booths at an airport. They allow you to swap one type of currency for another, or in the case of blockchain, one type of asset for another. However, just like some exchange booths can be scammy, not all cross-chain bridges have robust security measures. Understanding how these work is crucial for your safety.
Identifying Vulnerabilities in Cross-Chain Bridges
Just like a busy market vendor checks their cash for fakes, you should also vet the bridges you’re using. The most common vulnerabilities include coding flaws and poor smart contract implementations. CoinGecko’s 2025 data reveals that security audits are not just recommended; they’re necessary.
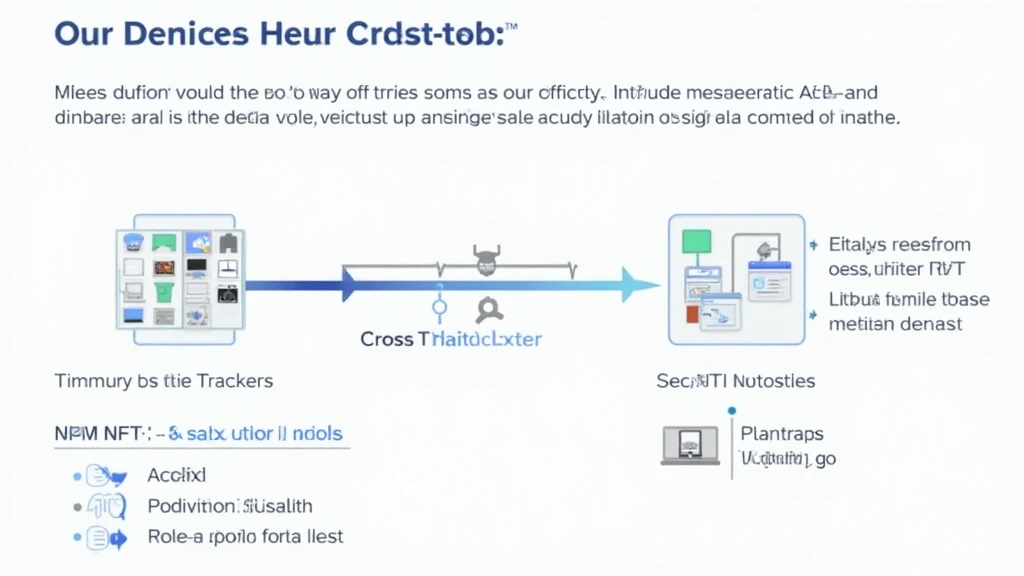
The Importance of Security Audits
Think of audits like a health checkup for your favorite restaurant. Just as you wouldn’t eat at a place with a bad hygiene score, you shouldn’t trust a cross-chain bridge without a thorough security inspection. Utilizing tools like the HIBT NFT Portfolio Tracker can help ensure your assets are protected.
Best Practices for Secure Transactions
To keep your assets safe, always conduct transactions on well-known and audited platforms. Additionally, using hardware wallets like Ledger Nano X can significantly lower the risk of private key exposure by about 70%. It’s like having a safe deposit box for your digital cash.
In conclusion, understanding cross-chain bridges and their risks is essential in today’s crypto world. The HIBT NFT Portfolio Tracker can enhance your transaction security and provide valuable insights into your investment portfolio. For more information, download our comprehensive toolkit for cross-chain security.