Introduction
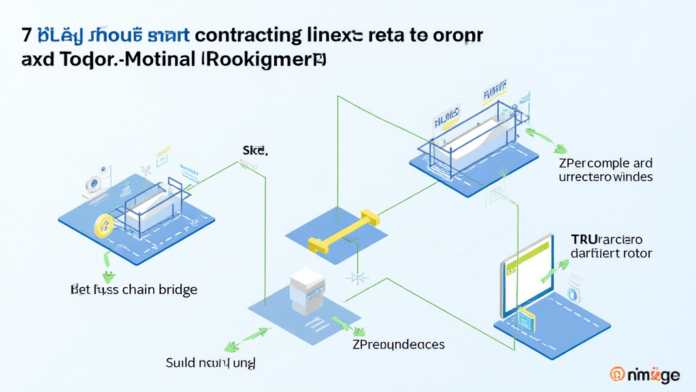
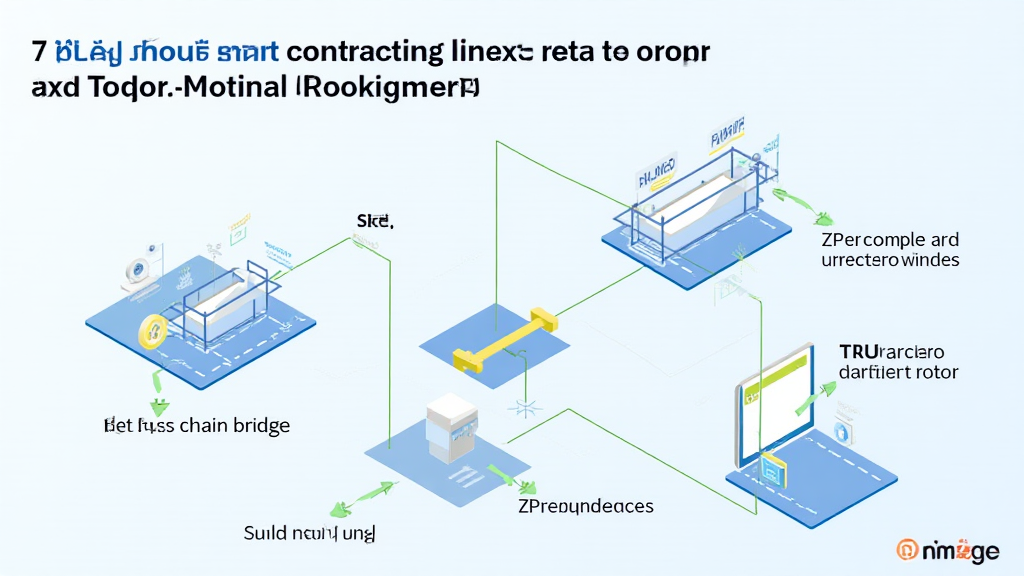
According to Chainalysis data from 2025, a staggering 73% of cross-chain bridges have vulnerabilities. With the rise of decentralized finance (DeFi) and cross-chain interoperability, ensuring the security of these bridges has never been more critical. The tools and methods available for debugging smart contracts are essential in preventing losses from exploitation.
Understanding Cross-Chain Bridges: A Layman’s Perspective
Think of cross-chain bridges as currency exchange booths in a busy market. Just like you wouldn’t want to hand over your cash to an untrustworthy exchange, you shouldn’t trust a cross-chain bridge without ensuring its security. This section dives into user concerns about the feasibility and security of these bridges.
The Role of Debugging Tools in Enhancing Security
Debugging tools for smart contracts can be likened to a thorough security check before hitting the road. Just as you check your car’s brakes, using tools such as MythX or Slither helps developers identify vulnerabilities before they lead to significant losses. Here’s what developers need to know about these tools and their application in the blockchain development process.
Zero Knowledge Proof Applications: The Ultimate Privacy Shield
Imagine sharing a secret but only revealing necessary details! This is what zero-knowledge proofs (ZKPs) offer in blockchain technology. This section explains how ZKPs enhance privacy and security in transactions, and why they are crucial for users concerned about data exposure.
The Future of DeFi Regulation in Singapore by 2025
In light of evolving DeFi platforms and user security concerns, Singapore is taking strides towards effective regulation by 2025. We will explore what these regulations mean for developers and users in Singapore’s blockchain space, focusing on how compliance will interact with tools for debugging smart contracts.
Conclusion
To summarize, ensuring the security of cross-chain bridges and smart contracts is vital for the future of blockchain interoperability. The tools and methods available for debugging smart contracts are instrumental in preventing vulnerabilities. For a comprehensive toolkit that lowers your risk when deploying these technologies, download our security toolkit today.
References
For further reading, check out the cross-chain security white paper and other resources at HIBT.
Risk Disclaimer: This article does not constitute investment advice. Please consult local regulatory bodies such as MAS or SEC before proceeding.
Tools like Ledger Nano X can significantly reduce private key exposure risks, securing your digital assets.